Background
With the explosion of mobile applications, Android, as an open-source mobile operating system, has exposed more and more security issues to its system and apps. Hackers can use rooted mobile phones to attack APP, modify APP business logic, and even use APP as a portal to steal user data or even directly steal money.
As an important part of environmental detection, Root detection plays a vital role in APP security protection.
There are some open source anti-root solutions on the market that detects the feature of the different root mechanisms, such as Magisk or SuperSU. It also checks whether there are some sensitive directories that can be accessed. However, there is no obfuscation of the code or other protections which means many anti-root solutions can be easily bypassed.
This article demonstrates how to bypass rootbeer’s anti-root mechanism.
Environment
- Root Machine with Magisk Hide
- Windows or MacOS
- RootBeer Sample app
Procedure
- Install RootBeer Sample app(the Sample app) from Google Play Store.
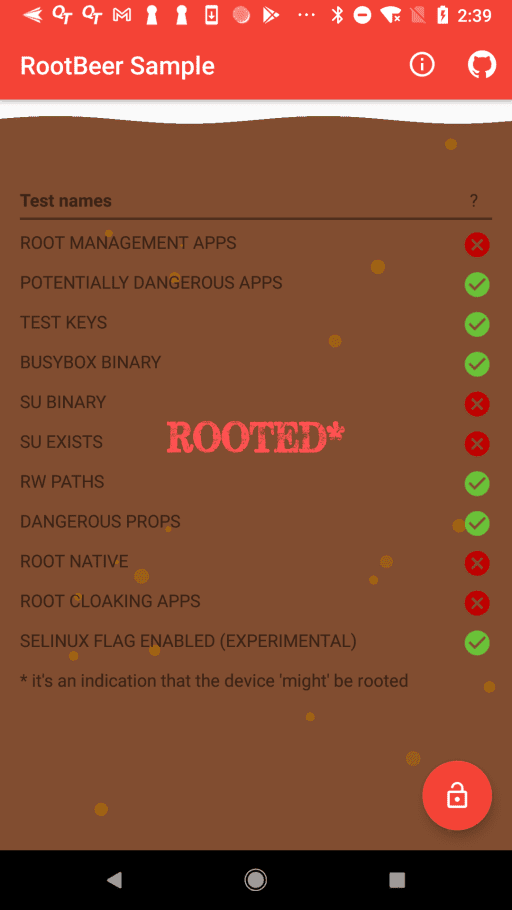
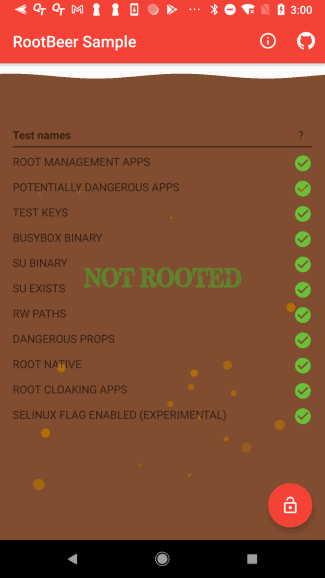
https://play.google.com/store/apps/details?id=com.scottyab.rootbeer.sample - Run the Sample app to check the root status.
-
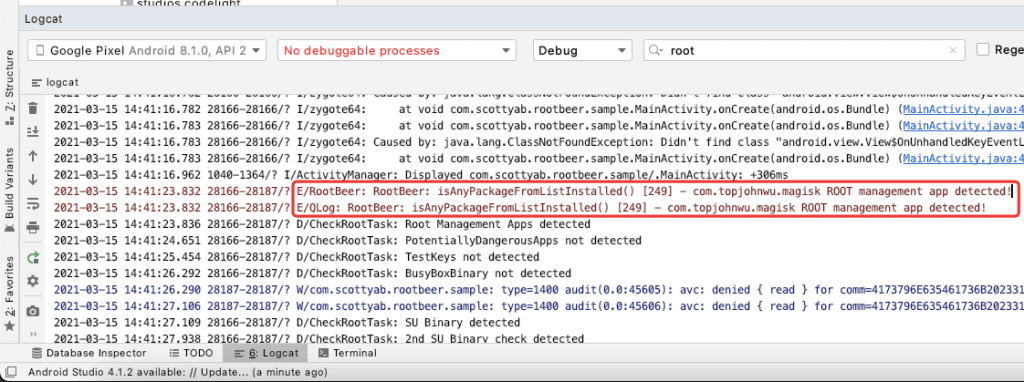
Use Android Studio to debug the Sample app. We can find some method names for us to trace.
-
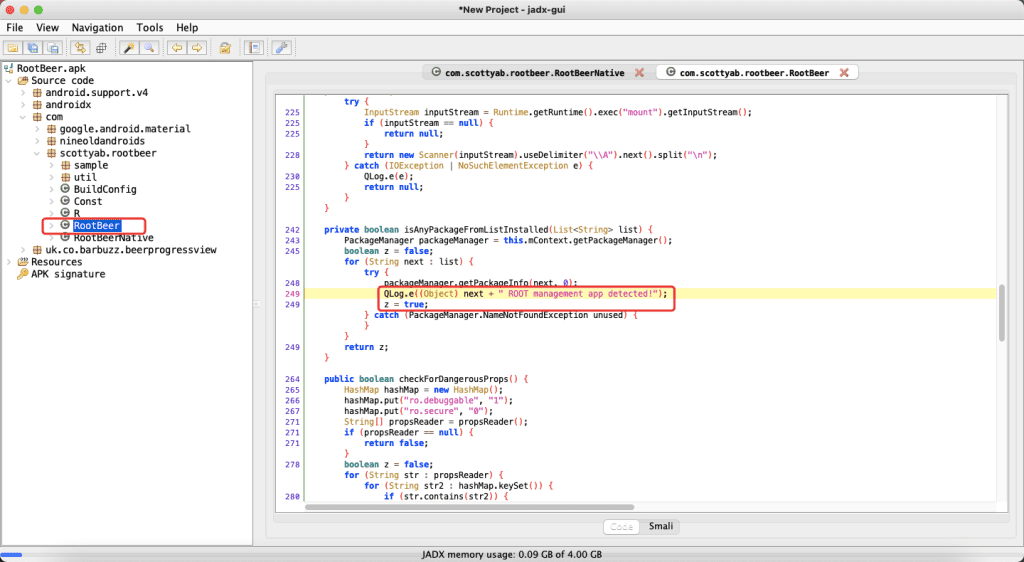
Use decompiling tools like JADX to check out the code and search for our method names from previous step. Study the logic and found out the key part that was used to return the value of whether it is rooted or not.
It was using variable z to decide the root status. All we need to do is to manually change z=true to z=false.
-
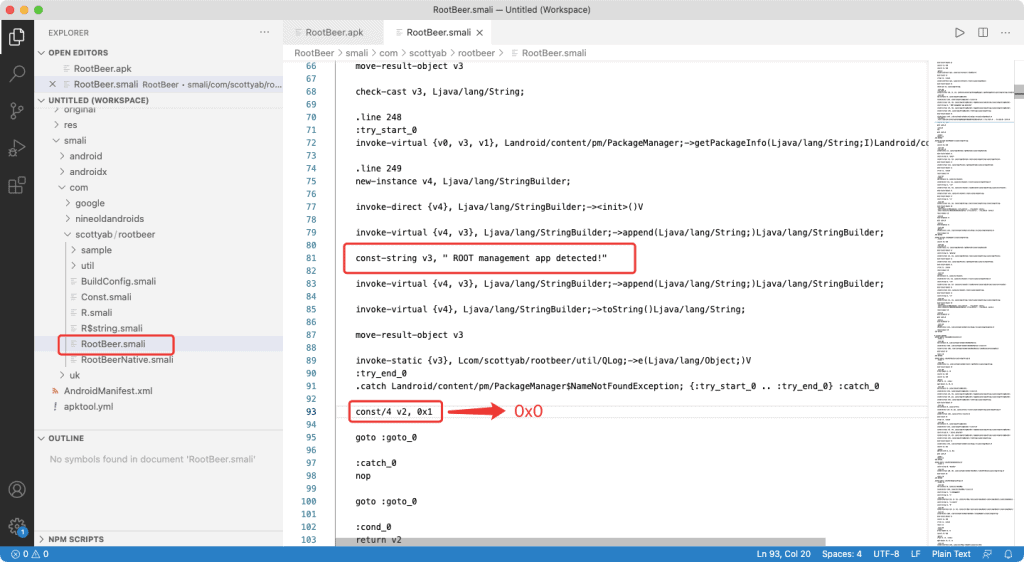
Use Apktool to decompile the code to Smali code so that we can make changes and repackage it.
Command line: Apktool d RootBeer.apk
-
According to the Sample app, we know RootBeer is checking many root related factors to decide whether the device is rooted or not. Here we only need to fix two of the test logics since we can use Magisk Hide to hide the other root indications. Obviously, we can change all of them manually.
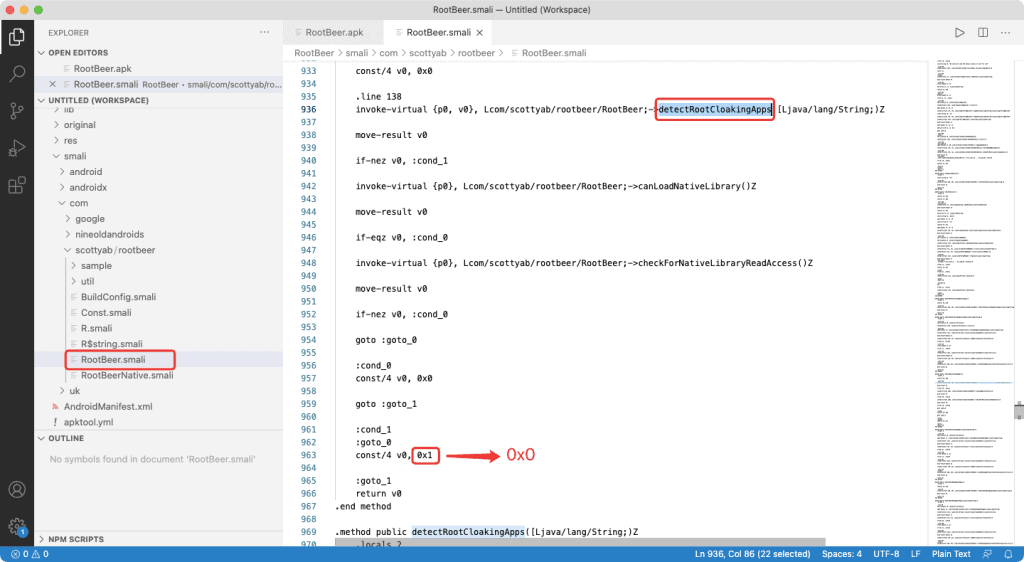
The precise location of the code we were changing:
detectRootCloakingApps() – change const/4 v0, 0x1 -> const/4 v0, 0x0.
isAnyPackageFromListInstalled() – change const/4 v0, 0x1 -> const/4 v0, 0x0.
-
Then we just need to repackage and sign the apk. Now after installation with the help of Magisk Hide, the Sample app will not be able to detect any root mechanism that we are currently using.
Command line:
Apktool b RootBeer -o rootbeer_crack.apk
Solution
At SecIron, we provide professional mobile app hardening and other protection product and services
We protect mobile apps against static attacks and threats like decompilation, repackaging, etc. as well as dynamic attacks and threats like root/jailbreak, debug, hook and much more.